BeyondTrust. Managing Shared Accounts for Privileged Users: 5 Best Practices for Achieving Control and Accountability
April 5, 2022 - 6 minutes readMany IT organizations use shared accounts for privileged users, administrators, services, or applications so that they can have the access they need to perform an activity. Account sharing often entails use of the same account credentials to authenticate multiple users. Without proper management controls in place, the practice of account sharing presents significant security and compliance risks from intentional, accidental, or indirect misuse of shared privileges.
Even for the savviest IT teams, the task of managing shared accounts introduces complexities and risks:
- Embedded and hardcoded passwords present opportunities for misuse by both insiders and external attackers on the network.
- Passwords for application-to-application and application-to-database access are often left out of management strategies.
- Static passwords can easily leave the organization, and manual password rotation tends to be unreliable.
- Auditing and reporting on privileged access is complex and time consuming, since it is difficult, or impossible, to attribute any of the session activities of a shared account back to a single identity.
5 Best Practices: Gaining Accountability over Shared Accounts
Recent breaches exploiting privileged credentials have underscored the imperative to improve control and accountability over access to shared accounts. So, how do organizations ensure accountability of shared privileged accounts to meet compliance and security requirements without impacting administrator productivity? Consider these five best practices:
1. Deploy a single, hardened, appliance-based enterprise password management solution with broad platform support and functionality
Ensure your solution provider deploys their privileged password and session management solution in a single hardened or virtual appliance that features broad support of operating systems, databases, applications, devices, and directories. Remember, it’s more than just user passwords. Consider the complexity and risk of managing privileged passwords for service accounts, between applications (A2A), and to databases (A2DB). Everything your solution provider does should be about reducing the interfaces and administration required.
2. Discover and profile to give greater control
Leverage a distributed network discovery engine to scan, identify, and profile all users and services – and then automatically bring the systems and accounts under management. Discovering and profiling all known and unknown assets, shared accounts, user accounts, and service accounts, and then placing them under intelligent rules gives greater control and significantly improved consistency of policy enforcement.
3. Monitor and manage sessions, with full playback
Your solution should record privileged sessions in real-time via a proxy session monitoring service for SSH and RDP without revealing the password. DVR-style playback provides detailed auditing of shared account access, helping to meet password protection and audit regulations for compliance mandates listed in SOX, HIPAA, GLBA, PCI DSS, FDCC, FISMA, and others.
The solution should also be able to identify suspicious sessions in real-time and initiate a workflow to pause or terminate them.
4. Make it easy on yourself by using standard desktop tools
Driving a strong, consistent organizational security posture is a challenging effort. Introducing new workflows makes this effort even harder. Having to log in to a solution each time a user needs to access a system creates adoption and training challenges.
Solutions must support standard desktop tools such as PuTTY, RDP, SSH and Microsoft Terminal Services Client. This means you can leverage commonly used management tools so your user can smoothly work within their established workflows.,
5. Gain greater insights through reporting and analytics
Look for a single pane-of-glass to collect, correlate, trend, and analyze key metrics. You need to understand key insights into:
- Privileged accounts
- Password age
- SSH keys
- Service accounts running with user accounts
- User accounts with administrative rights on Windows/Mac and Unix/Linux
- Remote Access Tools
These insights help you identify areas that require action before they become a security concern.
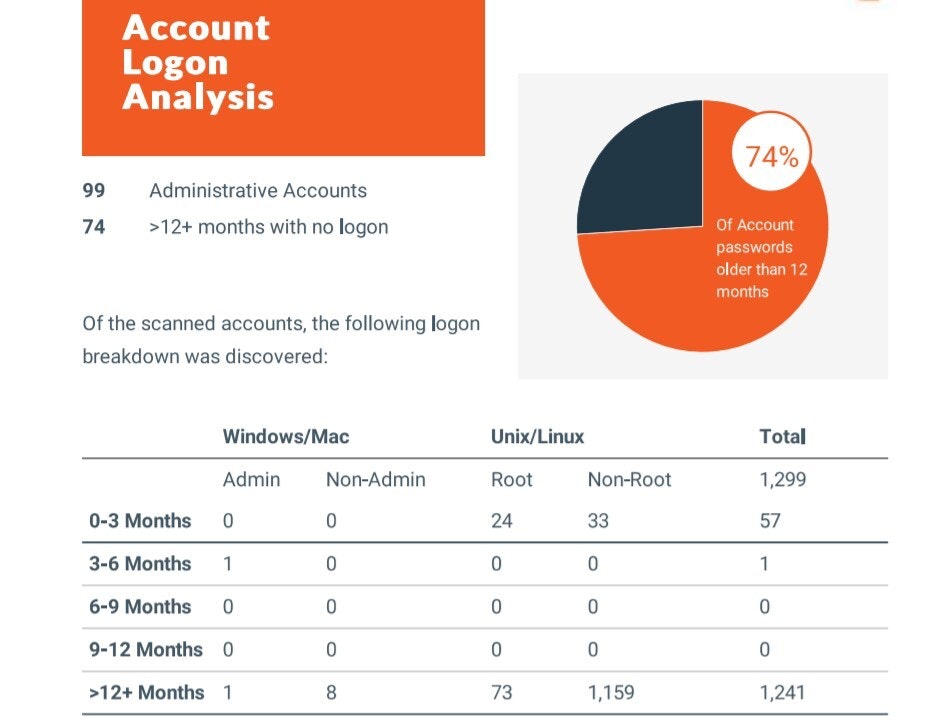
Solutions for Securing Shared Privileged Accounts
BeyondTrust Password Safe automates password and session management, providing secure access control, auditing, alerting and recording for any privileged account – from local or shared administrator to service to application accounts.
Team Passwords is a feature designed to securely store credentials owned by small groups within Password Safe, in a fully auditable controlled environment. This feature delivers secure password practices teams in the organization outside of traditional privileged admin user roles.
By improving the accountability and control over privileged access with Password Safe, IT organizations can reduce security risks and achieve compliance objectives.
Source: BeyondTrust
The post BeyondTrust. Managing Shared Accounts for Privileged Users: 5 Best Practices for Achieving Control and Accountability appeared first on NSS.
Powered by WPeMatico