Sophos. Searching for malicious PowerShell executions with Intercept X
April 28, 2019 - 2 minutes readIs PowerShell bad? Not necessarily. In fact, most PowerShell executions are not malicious, but PowerShell can be (and often is) taken advantage of.
The new Sophos EDR capabilities offer the ability to track down malicious executions that otherwise may remain hidden. For example, executions which use the encoded command argument are more likely to be associated with bad behavior and are less common in good executions.
With Intercept X Advanced with EDR 1.1, analysts can easily search for PowerShell commands, including encoded command arguments.
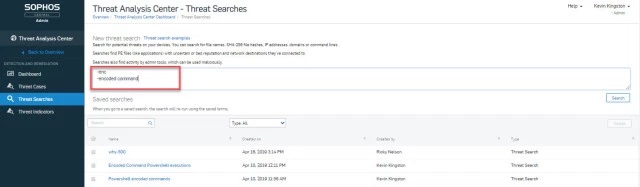
You can look for other suspicious PowerShell executions besides encoded commands such as policy bypass (-Exec Bypass), missing information (-NoLogo, -NoProfile), and more.
These new capabilities have also been added to the Intercept X Advanced for Server with EDR Early Access Program (EAP) so participants can start using these new features on their servers.
PowerShell features previously included in Intercept X
Intercept X already blocks known malicious PowerShell activity. The Application Lockdown feature automatically terminates a protected application based on its behavior. For example, when an Office application is leveraged to launch PowerShell, access the WMI, run a macro to install arbitrary code, or manipulate critical system areas, Sophos Intercept X will block the malicious action – even when the attack doesn’t spawn a child process. It will also prevent malicious PowerShell code executions via Dynamic Data Exchange too. Learn more about exploit protection with Intercept X.
Finally, if PowerShell appears to be involved with a detection it is referenced in a Threat Case where the command line executed can be analyzed.
The post Sophos. Searching for malicious PowerShell executions with Intercept X appeared first on NSS.
Powered by WPeMatico