SealPath.The real impact of ransomware on businesses
November 10, 2022 - 9 minutes readome years ago we saw how a new wave and trend in ransomware attacks. In the attacks on the City of Pensacola and the New Jersey synagogue, not only had the data been encrypted, it had been exfiltrated and the attackers were demanding a ransom for not making it public.
The impact of these types of attacks goes beyond encryption and the need to recover backups, but puts companies at risk of suffering significant financial and reputational losses from lawsuits, litigation and non-compliance with regulations.
In the last yeats we saw how this trend has gone further and some organizations have even decided to pay attackers to avoid penalties or litigation.
Publication of company data by DDoSecrets activists
Some time ago, the activists known as “Distributed Denial of Secrets” DDoSecrets published on their website more than 1 terabyte of sensitive data that were exfiltrated in ransomware attacks and had been picked up from “dark web” sites. This data includes more than 750,000 emails and documents from different companies. Additionally, this group of transparency activists is privately offering massive amounts of business data to a select group of journalists and academic researchers. These data come from companies in different sectors such as financial, pharmaceutical, energy, manufacturing, retail, software, real estate.

According to DDoSecrets, if there is information, technical data, specifications, etc. of a company in any sector that can accelerate the progress of a certain industry or make people’s lives safer, they have a duty to make this information available to journalists and people in academia so that they know the dark way in which these companies typically operate.
1.2 GB of published data from the Scottish Environmental Protection Agency
The Scottish Environment Protection Agency (SEPA) had confirmed that, after refusing to pay a ransom, an organized group of hackers had published 1.2 GB of data extracted as a result of a ransomware attack. According to the agency at least 4,000 files have been stolen that included workers’ personal information purchasing information, documents on ongoing projects, and information related to the agency’s corporate plans.
Data published after exfiltrations in financial and wealth management companies
At the end of 2020 stolen data from different financial and wealth management companies published were found on sites operated by Sodinokibi and NetWalker ransomware gangs. The way of operating is the one that we have already commented, first the confidential data of these organizations are stolen to later request a ransom for not publishing this data. This data contained employee files, audits, financial documents, payroll data, customer files, etc. Even the Sodinokibi criminal gang auctioned this data on different forums on the Dark Web.
Attacks targeting executives to extract confidential information
Ransomware gangs are targeting the computers or devices of senior company executives to obtain sensitive information that they can later use to extort money from companies for hefty ransoms. According to ZDNet, discovered this tactic after talking to a company that had paid a multi-million dollar ransom to the Clop ransomware gang. After several calls, they discovered that this was not an isolated case.
This group focuses on extracting files and emails from executives that can be useful to threaten them and put the company’s management under pressure to obtain a ransom. Ransomware attacks usually go for the “crown jewels” or those data that have the most value for the company, so it is not surprising that sooner or later they focused their objectives on the group of company executives.
27% of organizations decide to pay the ransom
According to a survey conducted by security maker Crowdstrike, among all organizations attacked by ransomware 27% decide to pay the ransom, with the average being USD 1.1M. Many decide to make the payment to avoid fines for non-compliance with regulations, or to face litigation and millionaire lawsuits or simply to avoid further scandals that can seriously damage their reputation.
For example, the University Hospital of New Jersey paid 670K USD to the SunCrypt ransomware band to prevent the publication of 240 GB of stolen data including patient data. After 48,000 documents pertaining to the hospital were published, a representative of the hospital contacted the attackers via its payment portal on the dark web to negotiate the cessation of new publications of patient data.
To pay or not to pay the ransom
Of course, the FBI strongly advises against paying a ransom, partly because it does not guarantee that the criminal organization won’t have access again to your data or that it won’t be published. Furthermore, it incites attackers to increase their actions against other organizations and to continue profiting from extortion. In any case, the FBI understands that when companies are unable to continue with their functions, they will evaluate all options to protect their shareholders, employees and customers. On the other hand, the controversy arises as to whether paying a ransom may violate laws on financing terrorist activities, money laundering, etc.
Data encryption as a means to protect against a ransomware attack
Data encryption protects information wherever it moves. If the data has been encrypted, it will be inaccessible or useless to cybercriminals. The data may be re-encrypted by the malware, but if it is extracted, they cannot be published as is happening in recent attacks where data is extracted in clear and extorted with the potential publication of the same.
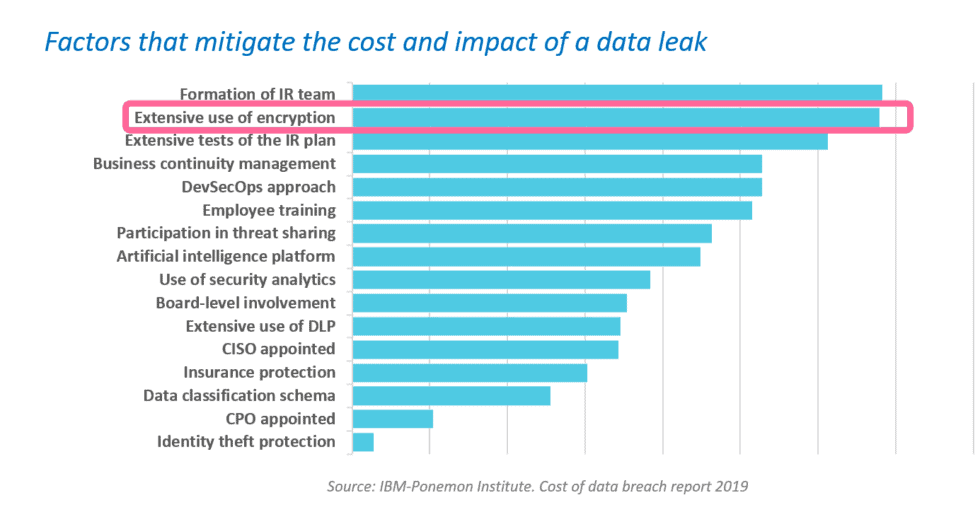
Organizations must not only consider a traditional encryption solution to protect themselves from these attacks, but also one that have control on access and identity so makes it possible to restrict access permissions (View, edit, print, etc.).
How SealPath can help prevent the effects of a ransmoware attack
With a data-centric security solution like SealPath:
- The data will remain protected when is at rest, in transit and in use.
- It is possible to limit access permissions, so that if a document is shared with a third party, they can open it and work with the document without having to unprotect it, thus the copies remain encrypted wherever they behave.
- It is possible to control the identity of the people who can access a certain file. In this way, if an identity has been compromised, it is possible to revoke access to the documents to it.

SealPath also offers a complete audit of accesses to protected information, so that users’ activity on sensitive documentation of the organization can be seen. If you want to know more, click below, and you will see the features of SealPath’s data protection solution.
Don’t wait to ask yourself whether or not the ransom is worth paying, put the means first to have your data safe and under control in any location and safe from possible ransomware attacks. Contact our team here and we will help you as soon as possible.
Source: SealPath
The post SealPath.The real impact of ransomware on businesses appeared first on NSS.
Powered by WPeMatico